Access restricted or blocked websites in your school and college using web proxy. Your activity will be hidden.
Using Hidemyass Web Proxy Service.
Using Proxy ServersUsing Hidemyass Web Proxy Service.
- Open website : http://www.hidemyass.com/
- Form Web Proxy section, turn SSL Security on.
- Enter the website you want to access and hit Hide my ass button.
- You can also open website without open hidemyass.com every time
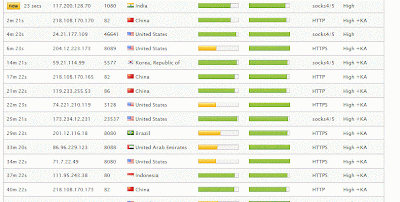
- Open link: http://www.hidemyass.com/proxy-list/
- Uncheck the anonymity level:None, Low Medium
- Uncheck the Speed :Slow, Medium.
- Uncheck the Connection Time : Slow , Medium
- Now click on update results
- It will now list fast and anonymous proxy servers.
- Now open your web browser like Mozilla Firefox, Chrome, IE, etc
- And set Manual Proxy as from the list you got from hidemyass.com and apply
If you want to learn, how to set manual proxy in Web browsers check my blog again.